SOLUTIONS | SPORTS & ENTERTAINMENT
KEEP YOUR FANS CHEERING
Deliver an unforgettable fan experience with seamless commerce throughout your entire venue - including next-gen POS solutions, mobile ordering, and loyalty.
Deliver an unforgettable fan experience with seamless commerce throughout your entire venue - including next-gen POS solutions, mobile ordering, and loyalty.
As the preferred choice of industry leaders, we deliver the most comprehensive end-to-end solution to connect all your revenue streams across your entire venue.
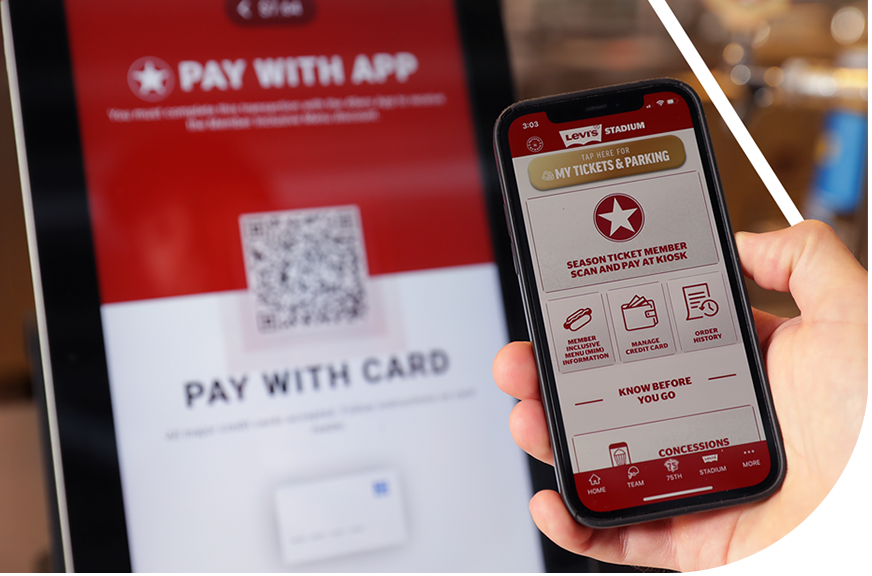
A slam dunk for everything F&B. From traditional point-of-sale and kiosk ordering to mobile and contactless solutions, we’ve got you covered from front-of-house to back-of-house so fans don’t miss a minute of the action.
Whether you have an existing retail solution or looking for something new, we integrate with dozens of software providers to help you reimagine retail.

Avoid traffic jams in the parking lot. Keep traffic moving upon arrival and reduce friction in your parking lots by accepting all payment types with a mobile POS.

Deliver a seamless fan experience from the start. Our integrations with the top ticketing platforms give you a complete end-to-end solution so you can focus on the event, and fans can focus on making memories.





See how Shift4 is helping Allegiant Stadium simplify operations and deliver a first-class fan experience at their world-class venue.
Proudly empowering payments and customer experiences at over 50% of major league venues and NCAA arenas.
























See how Shift4 helped Los Angeles Football Club elevate the guest experience at BMO Stadium.
Shift4 can help you create an experience marketplace to generate new revenue streams.
Have complete control of your venue. Our cloud-based back office puts actionable data at your fingertips to help you manage every aspect of your business.

See how DC United is leveraging Shift4 technology and real-time data to personalize offers, streamline operations, and improve their bottom line.
We integrate with the key sports and entertainment software solutions.





Your customers’ data will always be protected by state-of-the-art security technology, including EMV, PCI-validated point-to-point encryption (P2PE), and advanced tokenization.

With our one-stop-shop approach, Shift4 can offer you the lowest total cost to accept credit card payments – including free contactless EMV terminals, free mobile devices, and waived fees.

Enjoy white-glove service every step of the way — starting with installation by our experienced technicians to ongoing support from our in-house team — available 24 hours a day, seven days a week.
See how the Florida Gators are winning over fans with game day experiences powered by Shift4’s technology.

See how the Tampa Bay Rays shift to a mobile-focused fan experience and fuel growth with Shift4’s technology.
